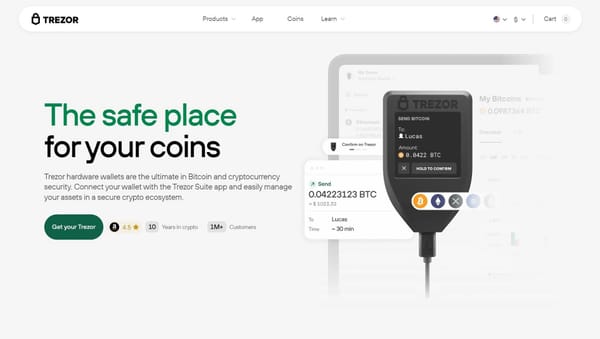
Trezor Login – Secure Access to Your Crypto Wallet
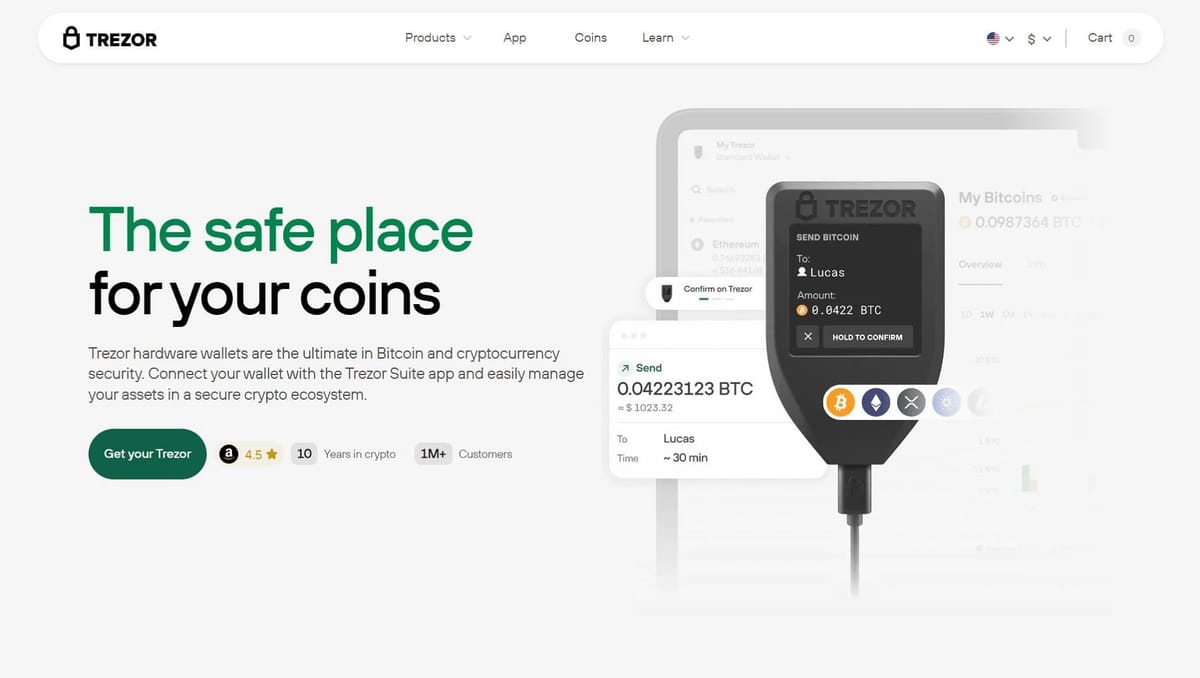
Accessing your Trezor wallet is simple, safe, and designed to protect your cryptocurrency at every step. Unlike traditional online accounts, Trezor does not use usernames or passwords stored on a server. Instead, your login process relies on your hardware wallet, PIN, and optionally a passphrase, ensuring your funds remain completely under your control.
Why Trezor Login Is Different
Most online wallets store private keys on the cloud, leaving them vulnerable to hacks. Trezor works differently: your private keys never leave your device. Logging in to your Trezor wallet means connecting your hardware wallet to Trezor Suite or compatible apps, verifying transactions directly on your device, and confirming your identity with your secure PIN. This ensures that even if your computer is compromised, your crypto cannot be accessed by anyone else.
How to Log In to Trezor
- Go to Trezor Suite or Supported App: Start by opening the official Trezor Suite app on your computer or using a compatible web interface.
- Connect Your Trezor Device: Plug your Trezor hardware wallet into your computer using the USB cable. The device will power on and show a welcome screen.
- Enter Your PIN: Your PIN unlocks your Trezor. Each PIN is unique, and it is never transmitted or stored anywhere—your Trezor verifies it internally.
- Optional Passphrase: For additional security, you can add a passphrase. Think of it as a “13th word” to your recovery seed, giving you an extra layer of protection.
- Access Your Wallet: Once verified, your Trezor Suite interface will display your crypto balances, transaction history, and portfolio overview, giving you full control over your assets.
Tips for a Secure Trezor Login
- Always Use Official Software: Only log in through Trezor Suite or trusted third-party wallets that support Trezor. Avoid phishing sites.
- Never Share Your Recovery Seed: Your 12–24 word recovery seed is only needed to restore your wallet, never to log in.
- Keep Your Device Safe: Treat your Trezor like cash—physical access is required for login.
Logging In Across Devices
You can log in to your Trezor wallet on multiple computers using the same hardware device. The wallet is portable and secure, so you maintain control wherever you go. Each login still requires the physical device, your PIN, and optional passphrase verification.
Recovering Access
If your Trezor is lost or damaged, you can log in to a new device using your recovery seed. This allows you to regain full access to your funds safely. Always keep your recovery seed stored offline in a secure place, separate from your device.
Conclusion
Trezor Login combines ease of use with unmatched security, giving you peace of mind while managing your crypto. With your hardware wallet, PIN, and optional passphrase, you remain the only person in control of your digital assets. Logging in has never been simpler, safer, or more reliable.