Trezor™ Login | Secure Crypto®
Trezor Login – Accessing Your Cryptocurrency Securely
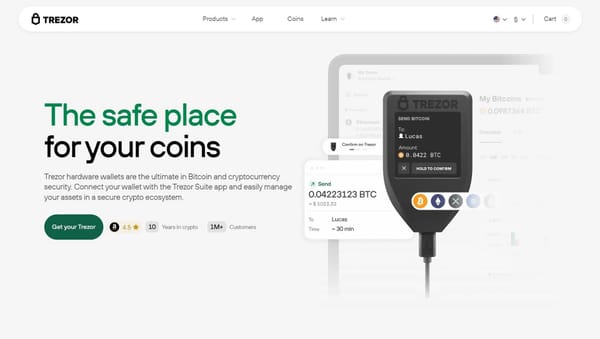
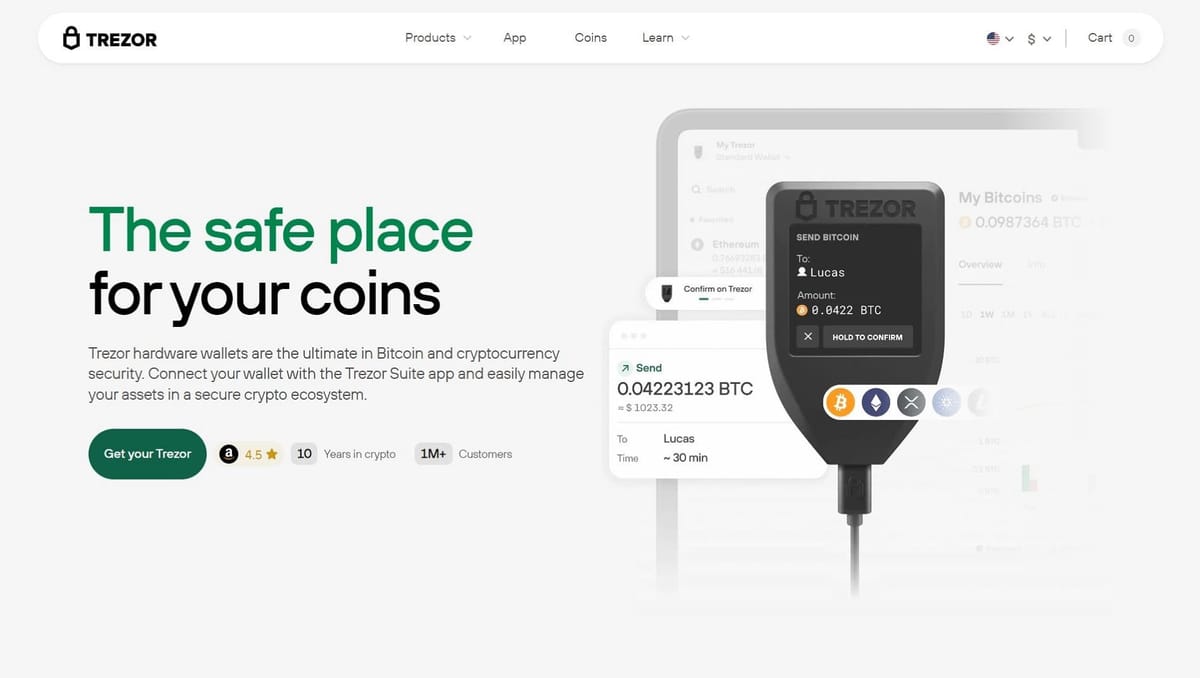
Unlike traditional online accounts, Trezor doesn’t use usernames or passwords to log in. Your Trezor hardware wallet keeps your private keys offline, meaning your crypto cannot be accessed directly via a website login. Instead, “logging in” to Trezor involves connecting your device to a trusted interface like Trezor Suite or a supported third-party wallet.
How Trezor Login Works:
- Connect Your Trezor Device
To access your crypto, plug your Trezor hardware wallet into your computer or mobile device using the USB cable. - Open Trezor Suite or Compatible Wallet
You can manage your assets through the Trezor Suite App (desktop or web) or supported crypto wallets like Electrum or MetaMask. The app will detect your device and prompt you to interact with it. - Enter Your PIN
Trezor requires a PIN code for every session. This ensures that only you can authorize access. The PIN is entered using a randomized on-screen grid to prevent keylogging attacks. - Optional Passphrase
For extra security, you can use a passphrase. This acts like an additional “word” added to your recovery seed, creating a hidden wallet accessible only with the passphrase. - Access Your Wallet
Once your device is verified and the PIN/passphrase entered, you can view balances, send and receive crypto, and manage multiple accounts. All sensitive operations, like signing transactions, happen on your Trezor device itself, so your private keys never leave the hardware wallet.
Important Notes About Trezor Login:
- Trezor does not store passwords or private keys online, so there’s no cloud login like a traditional web account.
- You can always restore your wallet on another Trezor device using your recovery seed if your device is lost or damaged.
- Only use official Trezor software (like Trezor Suite) to avoid phishing attacks.
Why Trezor Login is Secure:
The Trezor login process ensures that even if your computer is compromised, hackers cannot access your crypto. The device itself must confirm all actions, keeping your funds safe.